The Global Positioning System (GPS) is a satellite-based navigation system made up of a network of 24 satellites placed into orbit by the U.S. Department of Defense. GPS was originally intended for military applications, but in the 1980s, the government made the system available for civilian use. GPS works in any weather conditions, anywhere in the world, 24 hours a day. There are no subscription fees or setup charges to use GPS.
How it works
GPS satellites circle the earth twice a day in a very precise orbit and transmit signal information to earth. GPS receivers take this information and use triangulation to calculate the user's exact location. Essentially, the GPS receiver compares the time a signal was transmitted by a satellite with the time it was received. The time difference tells the GPS receiver how far away the satellite is. Now, with distance measurements from a few more satellites, the receiver can determine the user's position and display it on the unit's electronic map.
A GPS receiver must be locked on to the signal of at least three satellites to calculate a 2D position (latitude and longitude) and track movement. With four or more satellites in view, the receiver can determine the user's 3D position (latitude, longitude and altitude). Once the user's position has been determined, the GPS unit can calculate other information, such as speed, bearing, track, trip distance, distance to destination, sunrise and sunset time and more.
How accurate is GPS?
Today's GPS receivers are extremely accurate, thanks to their parallel multi-channel design. Garmin's 12 parallel channel receivers are quick to lock onto satellites when first turned on and they maintain strong locks, even in dense foliage or urban settings with tall buildings. Certain atmospheric factors and other sources of error can affect the accuracy of GPS receivers. Garmin® GPS receivers are accurate to within 15 meters on average.
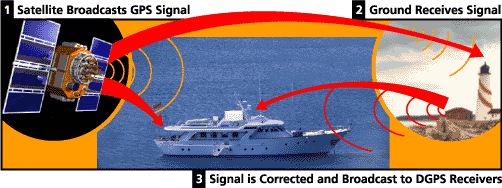 Newer Garmin GPS receivers with WAAS (Wide Area Augmentation System) capability can improve accuracy to less than three meters on average. No additional equipment or fees are required to take advantage of WAAS. Users can also get better accuracy with Differential GPS (DGPS), which corrects GPS signals to within an average of three to five meters. The U.S. Coast Guard operates the most common DGPS correction service. This system consists of a network of towers that receive GPS signals and transmit a corrected signal by beacon transmitters. In order to get the corrected signal, users must have a differential beacon receiver and beacon antenna in addition to their GPS.
Newer Garmin GPS receivers with WAAS (Wide Area Augmentation System) capability can improve accuracy to less than three meters on average. No additional equipment or fees are required to take advantage of WAAS. Users can also get better accuracy with Differential GPS (DGPS), which corrects GPS signals to within an average of three to five meters. The U.S. Coast Guard operates the most common DGPS correction service. This system consists of a network of towers that receive GPS signals and transmit a corrected signal by beacon transmitters. In order to get the corrected signal, users must have a differential beacon receiver and beacon antenna in addition to their GPS.
The GPS satellite system
The 24 satellites that make up the GPS space segment are orbiting the earth about 12,000 miles above us. They are constantly moving, making two complete orbits in less than 24 hours. These satellites are travelling at speeds of roughly 7,000 miles an hour.
GPS satellites are powered by solar energy. They have backup batteries onboard to keep them running in the event of a solar eclipse, when there's no solar power. Small rocket boosters on each satellite keep them flying in the correct path.
Here are some other interesting facts about the GPS satellites (also called NAVSTAR, the official U.S. Department of Defense name for GPS):
- The first GPS satellite was launched in 1978.
- A full constellation of 24 satellites was achieved in 1994.
- Each satellite is built to last about 10 years. Replacements are constantly being built and launched into orbit.
- A GPS satellite weighs approximately 2,000 pounds and is about 17 feet across with the solar panels extended.
- Transmitter power is only 50 watts or less.
What's the signal?
GPS satellites transmit two low power radio signals, designated L1 and L2. Civilian GPS uses the L1 frequency of 1575.42 MHz in the UHF band. The signals travel by line of sight, meaning they will pass through clouds, glass and plastic but will not go through most solid objects such as buildings and mountains.
A GPS signal contains three different bits of information — a pseudorandom code, ephemeris data and almanac data. The pseudorandom code is simply an I.D. code that identifies which satellite is transmitting information. You can view this number on your Garmin GPS unit's satellite page, as it identifies which satellites it's receiving.
Ephemeris data tells the GPS receiver where each GPS satellite should be at any time throughout the day. Each satellite transmits ephemeris data showing the orbital information for that satellite and for every other satellite in the system.
Almanac data, which is constantly transmitted by each satellite, contains important information about the status of the satellite (healthy or unhealthy), current date and time. This part of the signal is essential for determining a position.
Sources of GPS signal errors
Factors that can degrade the GPS signal and thus affect accuracy include the following:
- Ionosphere and troposphere delays — The satellite signal slows as it passes through the atmosphere. The GPS system uses a built-in model that calculates an average amount of delay to partially correct for this type of error.
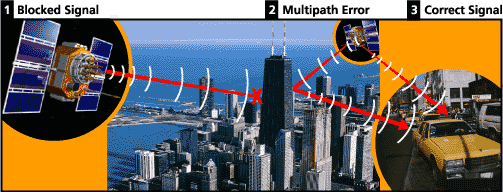
- Signal multipath — This occurs when the GPS signal is reflected off objects such as tall buildings or large rock surfaces before it reaches the receiver. This increases the travel time of the signal, thereby causing errors.
- Receiver clock errors — A receiver's built-in clock is not as accurate as the atomic clocks onboard the GPS satellites. Therefore, it may have very slight timing errors.
- Orbital errors — Also known as ephemeris errors, these are inaccuracies of the satellite's reported location.
- Number of satellites visible — The more satellites a GPS receiver can "see," the better the accuracy. Buildings, terrain, electronic interference, or sometimes even dense foliage can block signal reception, causing position errors or possibly no position reading at all. GPS units typically will not work indoors, underwater or underground.
- Satellite geometry/shading — This refers to the relative position of the satellites at any given time. Ideal satellite geometry exists when the satellites are located at wide angles relative to each other. Poor geometry results when the satellites are located in a line or in a tight grouping.
- Intentional degradation of the satellite signal — Selective Availability (SA) is an intentional degradation of the signal once imposed by the U.S. Department of Defense. SA was intended to prevent military adversaries from using the highly accurate GPS signals. The government turned off SA in May 2000, which significantly improved the accuracy of civilian GPS receivers.




 This is one another kuntilanak ghost which i write on this blog. as we know that kuntilanak ghost is the ost wanted ghost to view. i know it from te information that i got from the shutbox that there so many people who afraid with kuntilanak ghost. kuntilanak ghost also clasified as woman ghost. their appearance is looked like a wewe ghost and sundel bolong ghost. based on the kuntilanak ghost the movie kuntilanak was a ghost which is looking for her cildren. which die when she was pregnan. she was born in the yard.
This is one another kuntilanak ghost which i write on this blog. as we know that kuntilanak ghost is the ost wanted ghost to view. i know it from te information that i got from the shutbox that there so many people who afraid with kuntilanak ghost. kuntilanak ghost also clasified as woman ghost. their appearance is looked like a wewe ghost and sundel bolong ghost. based on the kuntilanak ghost the movie kuntilanak was a ghost which is looking for her cildren. which die when she was pregnan. she was born in the yard.
















 (This screen indicates incorrect credentials)
(This screen indicates incorrect credentials)









 The first thing your page obviously needs is an image. For blogs, the obvious image to first consider is your logo.
The first thing your page obviously needs is an image. For blogs, the obvious image to first consider is your logo. In the “Info” tab, you can type detailed information about your site such as the URL, the “overview” (so this would be a good place to enter any tagline or motto that your site has. MakeUseOf’s is “Cool Websites, Software and Internet Tips”).
In the “Info” tab, you can type detailed information about your site such as the URL, the “overview” (so this would be a good place to enter any tagline or motto that your site has. MakeUseOf’s is “Cool Websites, Software and Internet Tips”).












